Understanding CSRF: A Deep Dive into Cross-Site Request Forgery
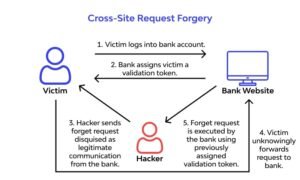
Cross-Site Request Forgery (CSRF), also known as Session Riding or XSRF, is a deceptive cyberattack that manipulates users into unknowingly executing unwanted actions on a trusted website. This exploit takes advantage of a web application’s inherent trust in a user’s authenticated session. By tricking a victim’s browser into sending forged requests—often via malicious emails or disguised links—attackers can perform unauthorized operations. Since these requests appear legitimate (coming from an authenticated user), websites may struggle to detect the fraud, leading to serious security risks.
Below, we’ll explore how CSRF attacks work, their consequences, and effective strategies to safeguard your web applications.
How Does a CSRF Attack Happen?
For a CSRF attack to succeed, three key conditions must typically be met:
-
Action-Based Vulnerability – The attacker targets a request that triggers a specific action, such as modifying account settings or administrative functions.
-
Cookie Reliance – The website depends solely on session cookies for authentication, without additional verification mechanisms.
-
Predictable Requests – The attacker can accurately guess the structure of the malicious request.
Once these conditions align, the attacker embeds the harmful request in a link or webpage, tricking the victim into triggering it while logged in.
Real-World Example of a CSRF Attack
Imagine receiving an email claiming to be from a shipping company, stating that your package is delayed and prompting you to click a link for resolution. You comply, landing on a familiar website—perhaps even your own. On the surface, everything seems normal.
However, suppose a plugin on that site (e.g., a music player) has a CSRF flaw. An attacker could craft a malicious link like
www.yourwebsite[.]com/music/settings?default_user=admin&anyonecanregister
If an admin clicks this link while logged in, the settings could silently change, granting registration privileges to anyone—including the attacker. This scenario underscores the importance of robust security measures, such as CSRF tokens and request origin validation.
CSRF vs. XSS: Key Differences
Though often confused, CSRF and Cross-Site Scripting (XSS) are distinct threats:
-
XSS injects malicious scripts into a webpage, executing in the victim’s browser to steal data (including CSRF tokens).
-
CSRF exploits the trust between a user’s browser and a website, tricking the browser into sending unauthorized requests.
A critical distinction? In CSRF, attackers usually don’t see the server’s response. However, if a site suffers from XSS, even strong CSRF protections can fail because XSS can steal tokens.
The Impact of CSRF Attacks
Successful CSRF attacks can have severe consequences, including:
-
Unauthorized fund transfers
-
Password and account takeovers
-
Theft of sensitive data (e.g., session cookies)
Attackers typically lure victims to malicious pages or embed harmful links in emails. Since requests appear legitimate (originating from the user’s browser), the damage depends on the victim’s privileges—admin accounts pose the highest risk.
How to Prevent CSRF Attacks
Mitigating CSRF requires a combination of user awareness and technical safeguards.
For Users:
-
Use unique, strong passwords for each account.
-
Log out of critical sites (e.g., banking, email) after use.
-
Avoid auto-saving passwords in browsers.
-
Verify links and attachments in emails before clicking.
For Developers:
-
Implement CSRF Tokens
-
Generate a unique, unpredictable token for each user session or action.
-
Embed tokens in forms or API requests and validate them server-side.
-
Reject requests with missing or mismatched tokens.
-
-
Leverage SameSite Cookies
-
Strict: Blocks cookies on all cross-site requests (highest security, but may disrupt navigation).
-
Lax: Allows cookies for safe (GET) requests but blocks risky (POST/PUT/DELETE) ones. Modern browsers default to Lax, improving security.
-
-
Referer Header Checks (With Caution)
-
Validate the
Refererheader to ensure requests originate from your domain. -
Note: This header can be spoofed or omitted, so don’t rely on it alone.
-
-
Configure CORS Properly
-
Use Cross-Origin Resource Sharing (CORS) policies to restrict unauthorized domains from accessing sensitive endpoints.
-
For high-risk actions (e.g., password changes), require reauthentication or CAPTCHA challenges for added security.
Final Thoughts
CSRF attacks exploit trust and authentication to manipulate users into performing unintended actions, potentially compromising data, finances, and system integrity. Combating CSRF is a shared responsibility: developers must implement robust defenses (tokens, SameSite cookies), while users should practice vigilant browsing habits.
As cyber threats evolve, staying informed and proactive is essential for a safer web experience.